Guest Access in Teams - More that just in Teams
- samanthaeasterday

- Feb 16, 2022
- 5 min read
I get asked often how to allow guest access aka federation for Microsoft Teams. Obviously, it is easy to change the settings in the Teams Admin Center, but there is wwwaayyy more to it.
Below are different areas to verify you have the correct settings set in your M365 deployment for guest access.
*This is for informational use only. I am NOT suggesting allowing guest access in every Teams environment is the right choice. So do your homework and make sure what you choose aligns with your security practices.
Allow guest access settings in Teams admin center
1) Go to your Teams Admin Center
2) Expand Users, go to Guest access
3) Click the drop down next to ‘Allow guest access in Teams’ and chose On
4) Go through the rest of the settings to turn On if needed

5) Under Messaging, turn On needed options

6) Click on External access
7) Click the drop down under ‘Select which external domains your users have access to:’
8) Select desired setting
a. If you chose ‘Allow only specific external domains’, add allowed domains

9) When both are on, outside Teams users can contact you using your sip address
10) If you check the box next to ‘External users with Teams accounts….’ Unmanaged external Teams users can start a conversation with people in your organization (less secure).

What can a federated user do?
Chat with users within your environment.
View files shared with them in chat messages.
What can’t a federated user do?
Search the user directory (excepting for email addresses and using Direct Routing/SIP).
Share files (remember, shared chat files go in the sharer’s OneDrive, and External Access does not enable a OneDrive, so there is nowhere to store the file).
Access Teams and Channel resources.
Participate in a Group chat (i.e., External Access is one to one chat ONLY so no starting a 1:1 and then adding someone).
View or set an Out of Office message / Status message.
Be blocked or Block someone.
Allow guest access settings in SharePoint admin center
1) Open SharePoint Admin Center
2) Expand Policies and click on Sharing
3) Select the level of sharing based on your needs

4) Expand ‘More external sharing settings’ and select settings needed

5) Select options to allow guests access to files and folders

Teams and SharePoint are connected in the following scenarios:
· When you create a new team from scratch, a new SharePoint site is created and connected to the team.
· When you create a new team from an existing Microsoft 365 group, the team is connected to the SharePoint site associated with the group.
· When you add Teams to an existing SharePoint site, that site is connected to the new team.
· When you create a new private or shared channel, a new SharePoint site is created and connected to that channel.
Guest access per site in SharePoint admin center
1) Open SharePoint admin center
2) Browse to Sites->Active sites
3) Click on the site you want to change
4) Click the Policies tab
5) Under External sharing, click Edit

6) Select preferred settings
The default settings are the Org wide settings you verified/set above. The permissions set here are for the site you chose

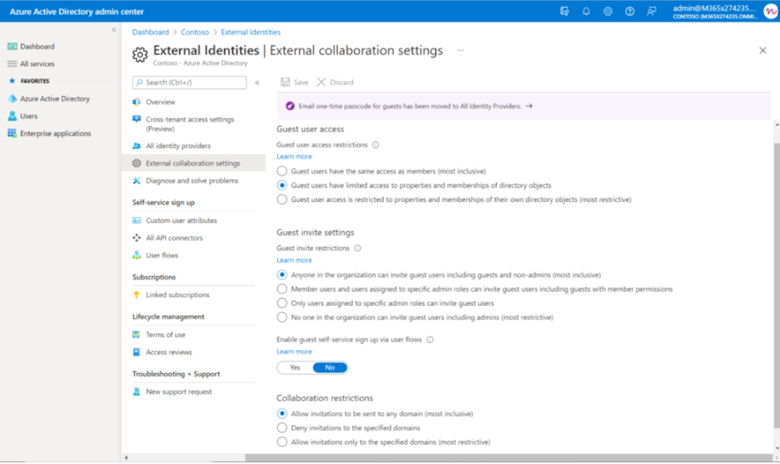
Allow guest access settings in Azure Active Directory admin center
7) Sign into Azure portal
8) Select Azure Active Directory
9) Browse to External Identities->External collaboration settings
10) Choose the level of restrictions for guests
Allow guest access settings in Microsoft 365 admin center
Microsoft Teams users Microsoft 365 Groups for team membership. For guest access to work in Teams, you need to set up Microsoft 365 Group guest settings.
1) Sign into Microsoft 365 admin center
2) Browse to Settings->Org settings
3) Under Office 365 Groups, both boxes should be checked

Monitoring external sharing activity
· Below are built-in alert policies concerning external sharing you can turn on in Office 365 Security & Compliance
Unusual external user file activity
Generates an alert when a large number of activities is performed on files by guest users in SharePoint or OneDrive. These activities include accessing, downloading, and deleting files.
Unusual volume of external file sharing
Generates an alert when an unusually large number of files in SharePoint or OneDrive is shared with people outside your organization.
Learn more about managing alerts.
· Configure sensitivity labels
What a sensitivity label is
When you assign a sensitivity label to content, it's like a stamp that's applied and is:
· Customizable. Specific to your organization and business needs, you can create categories for different levels of sensitive content in your organization. For example, Personal, Public, General, Confidential, and Highly Confidential.
· Clear text. Because a label is stored in clear text in the metadata for files and emails, third-party apps and services can read it and then apply their own protective actions, if required.
· Persistent. Because the label is stored in metadata for files and emails, the label roams with the content, no matter where it's saved or stored.
You can use sensitivity labels to:
· Provide protection settings that include encryption and content markings. For example, apply a "Confidential" label to a document or email, and that label encrypts the content and applies a "Confidential" watermark.
· Protect content in Office apps across different platforms and devices. Supported by Word, Excel, PowerPoint, and Outlook on the Office desktop apps and Office on the web. Supported on Windows, macOS, iOS, and Android.
· Protect content in third-party apps and services by using Microsoft Defender for Cloud Apps. With Defender for Cloud Apps, you can detect, classify, label, and protect content in third-party apps and services.
· Protect containers that include Teams, Microsoft 365 Groups, and SharePoint sites. For example, set privacy settings, external user access and external sharing, and access from unmanaged devices.
· Extend sensitivity labels to Power BI: When you turn on this capability, you can apply and view labels in Power BI, and protect data when it's saved outside the service.
· Extend sensitivity labels to assets in Azure Purview: When you turn on this capability, currently in preview, you can apply your sensitivity labels to files and schematized data assets in Azure Purview.
· Extend sensitivity labels to third-party apps and services. Using the Microsoft Information Protection SDK, third-party apps can read sensitivity labels and apply protection settings.
· Classify content without using any protection settings. You can also simply assign a label because of classifying the content. This provides users with a visual mapping of classification to your organization's label names and can use the labels to generate usage reports and see activity data for your sensitive content.
Additional guest access settings
Important to understand coexistence modes and where users will send/receive chats, calls, meetings, etc.
You can specify a coexistence mode:
· Teams only
· Islands (Teams and Skype for Business will coexist)
· Skype for Business only
· Skype for Business with Teams collaboration (Users receive chats and calls and schedule meetings in Skype for Business but use Teams for group collaboration)
· Skype for Business with Teams collaboration and meetings (Users receive chats and calls in Skype for Business but use Teams for group collaboration and to schedule meetings)
In Teams PowerShell, verify settings by running the below commands:
Get-CsTenantFederationConfiguration
Verify AllowedDomains lists all the allowed domains you entered or looks like below:

Get-CsExternalAccessPolicy
Verify your Global settings:




Comments